Charlie Miller gave a keynote at ARM TechCon on automotive security. He is regarded as one of the world’s most proficient hacker, although he is one of the good guys (a white hat in security parlance). He has a PhD, worked for the NSA, and is currently the senior security engineer at Uber. He works alongside Chris Valasek. You probably don’t know their names, but you may know of their work. They were the two engineers who took control of a Wired journalist’s Jeep, memorably reported as Hackers Remotely Kill a Jeep on the Highway—With Me in It. Or watch the video:
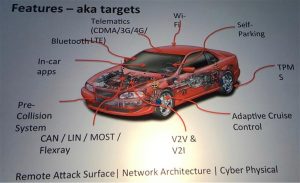

Figure 1. Smart car systems
Car Hacking History
Charlie said that car hacking started around 2010. Some academic researchers from University of Washington and UCSD plugged a device into the federally mandated on-board diagnostic port (OBD-II port) and could control the brakes, the windscreen wipers, and so on. They published their results under the catchy title Experimental Security Analysis of a Modern Automobile. This was not well received by either academia nor the car companies, who all pointed out that if you have physical access to the car (which you need to plug something into the OBD port) then of course you can do bad stuff. You could cut the brake lines, too.
So they took on that challenge. The next year, they produced another paper, even more catchily titled Comprehensive Experimental Analysis of Automotive Attack Surfaces. This time they attacked remotely and showed three ways to do it. The first involved Bluetooth (so was remote, but you had to be nearby), one was using a CD with a malicious MP3 track, and the most important was through OnStar. They could dial in from anywhere and take control. They could dial up the cellular modem in the car with a real phone, get the audio modulation tones, and then provide their own data. Charlies said it was “right out of an 80s TV show.”


Figure 2.
Charlie and Chris Get Interested
Charlie started to get interested in this. The academics had basically done everything but not given any technical details about what bugs they were exploiting, or even what kind of car it was (a Malibu). Nobody knew if it was just that one car, or all models, all cars.
In September 2012, Charlie and Chris got a DARPA Cyper Fast Track grant that gave them enough money to buy a car. They decided they wanted a car with automatic parking since then the steering would have to be controllable, too. And it had to be cheap. They got a Toyota Prius. Apparently it was the easiest sale ever for the dealership, since they didn’t care about the color or the options. Provided it had automatic parking, they would take it.
They rapidly discovered how to control the car once plugged into the OBD-II port. They could control the brakes, the windscreen wipers, the radio, and so on. Once again, nobody was impressed since they had physical access to the vehicle. It seemed that they would have to repeat everything.
The Jeep


Figure 3. ARM-based OMAP system
So this time, it was the Jeep. The short version of the story is that they discovered how to remotely compromise the vehicle, Wired magazine published the article, and a few days later Fiat Chrysler recalled 1.4 million vehicles at a cost of perhaps $14B.
But a lot of good came out of this since they released everything: the vulnerabilities, their code, and so on. Automotive hacking doesn’t scale if it is just the two of them. The academic researchers published stuff without details, and were largely ignored. Charlie and Chris told Chrysler that they would publish in nine months, and as far as they could see, Chrysler did nothing. But once the Wired article came out, the recall happened within a week. Clearly, publishing everything was the approach that got people protected the quickest.
At this point, they could control a lot of the vehicle but only if it was moving slowly. There were interlocks in the car to stop, for example, trying to automatically park the car when going 50mph on the freeway. But then they got to the stage where they could control the vehicle at any speed.


Figure 4. Automotive security: A hacker’s eye view
electronic features aka targets
How does this happen? It came about historically. Lots of electrical stuff got added to cars. Eventually, the weight of the wiring harness was a big issue (it affects both cost and fuel economy) and the automotive industry came up with CAN bus, a network. It had no security since it was only used for trusted things talking to trusted things. Then cars started to get connectivity to the outside world in various ways such as WiFi for passengers, wireless tire pressure monitoring, OnStar. So there were lots of signals coming into the car from outside. But people also wanted features like automatic emergency braking (AEB), lane following, autoparking. These mean that there is a computer than can control the brakes and control the steering wheel. Adaptive cruise control means there is a computer that controls how fast you are going. Lots of features. Or, as they call features in the security world, targets.
jeep head unit
The Jeep had lots of computers. The big one in the middle of the dashboard is known as the head unit. When Charlie and Chris started, they thought it would take a year or two to find and exploit a vulnerability. But they found something in three weeks and it took five minutes to exploit it. It wasn’t even really an exploit since they found an internet-facing interface that had a method called “execute”. You gave it a command, it would execute it. Inside the head-unit, there was a cellular modem connected to the Sprint network. Sprint wouldn’t allow traffic in from outside but they did allow one Sprint device to talk to another. So they bought a Sprint phone and could find vulnerable cars, get them to send their VIN, and find out what model they were. So they knew all the vulnerable cars but were limited to controlling the head unit. Charlies was tempted to hack into a Dodge Viper (a $100K+ car) and turn the radio up to full volume, but he resisted the temptation. But how could they really take control? Changing the radio channel is not much more than a prank.
head unit subsystemsInside the head unit were two subsystems. One was an ARM-based OMAP system, the other was V850-based (you’ve probably never heard of this but I know from my VaST days that this is an NEC processor widely used in automotive). The ARM system, to which the radio was connected, couldn’t access the CAN bus, only the V850 one. But it turns out that the ARM system can reflash the V850 one, and the code is not signed. Of course, if you try this and get it wrong, it bricks the whole head unit and you have to go back to the dealer to get it replaced. (“It’s a real lemon, this car.”) Eventually they got the brakes to work and so on.
You might ask, as they did, why the head unit is connected to the CAN bus at all. But people like speed-compensated volume (it turns up the volume as the car goes faster). People like being able to use their iPhone to start the car and get it warmed up. Cars are only going to get more connected.
The Wired article and video were made in the middle of this when they could control things like the radio and climate control, and also steering and brakes at low speed.
Other Hacks in the News
Charlies talked a little about other car hacking in the news, things you might have heard about:
Some dongles exist to plug into your car to allow fleet management, or lower insurance rates for good drivers. All the dongles analyzed by academics were vulnerable. So most things that are in your car you can’t do anything about, but here is one you can: don’t plug a dongle into your car.
Troy Hunt discovered that with a Nissan Leaf the authentication back to the server was just the VIN. So you could walk up to a Leaf, read the VIN through the windshield, and turn on the heated seats. Since it is an electric car it would drain the battery and it wouldn’t go. This wasn’t physically dangerous but the attack was really easy.
There was a famous Tesla hack. It also needed physical access and could not access the CAN bus, but they could control radio, windows, door locks. Not the really scary stuff. Then they found a web browser exploit which meant that they could reflash the CAN gateway and send arbitrary messages. Tesla fixed it, and made it so that the code needed to be signed. Since they can update over the air, it didn’t require a recall, it could just happen while all the owners were sleeping.
There were headlines about cars being stolen with electronic keys. But it turned out to be a low-technology approach. They stole the software for reprogramming keys, so they could then look up the VIN, create a key, open the car, and drive off.
All cars use proprietary message formats so an exploit in one car won’t work directly in another. With trucks this is not the case. The message formats are standardized among all manufacturers. So any attack on a truck will work on all trucks.
Summary
Charlie said they are trying to get ahead of the curve and communicate with car companies but “they don’t talk to us.” There are no white papers like there are from companies like Microsoft, about how their systems are designed for security. Hopefully things will get better but they are not in good shape right now.











